
May 15, 2018 | Events, Informative, RIsk Management News
Recently, I had the chance to spend some time at Walt Disney World in Orlando, Florida, when I attended the NAMIC conference in February. One session included a presentation by Barry Dillard, director of claims for Walt Disney World, where he shared the company’s approach to handling a wide variety of claims.
I sat down with their vice president of risk management to learn about some of the strategies they employ, and I had the opportunity to tour Walt Disney World itself to peek behind the curtain and see how this massive theme park creates the magic for its guests and cast members, while keeping everyone safe.
Believe it or not, the Walt Disney World Resort covers 40 square miles and is twice the size of Manhattan. Within its confines, this world-class attraction employs 75,000 cast members, each of whom play a critical role in spreading the Disney magic. Their emphasis on safety is both taught and caught, which is especially important when serving the millions of guests who visit the Disney attractions around the world.
The Walt Disney Company is extremely proactive in their risk management strategies — it truly is everyone’s responsibility — not just the realm of those at the corporate level. As is often the case in life, the simplest things can make the biggest difference. Merely walking the parks, hotels, shops and restaurants can yield valuable information, allowing cast members to identify small issues before they become larger ones. Even in one of the most magical places on earth – reality tends to intrude.
Unexpected risks arise every day and training plays a key role in mitigating them. Hackers are constantly devising new ways to access company information or hold it for ransom. The use of ransomware is expected to increase 350% this year, so being vigilant and backing up data has never been more important.
The number of shooting incidents in businesses and other settings is increasing at an alarming rate. Knowing what to look for and how to respond in these situations can literally be the difference between life and death.
For better or worse, new risks are changing our behavior — how observant we are in open spaces of our surroundings, what we post on social media, where and how we protect our personal information, what we open online and how we train our staffs. It really is the smallest things that can make the biggest difference in keeping people safe.
Source: PropertyCasualty360
Author: Patricia L. Harman

Mar 19, 2018 | Blog-All, RIsk Management News
Global risk managers must be prepared to mitigate their company’s exposures in these key areas over the next year.
This is undoubtedly a prosperous period for the world economy, but the recent volatility in global stock markets is an indicator that times may be changing. The World Bank has forecast global economic growth of 3.1% for 2018, which will obviously benefit businesses.
Global transformations
At the same time, an improving business environment brings with it the prospects of wage inflation, rising interest rates, and the end of cheap money. A couple of weeks ago, U.S. stocks reacted dramatically to figures that showed U.S. wages rising faster than expected. This clearly demonstrated how jittery the markets are about the end of a loose monetary policy.
In addition to these macroeconomic developments, other significant changes are afoot. The established political order is being questioned in the United States and Europe, tensions are rising again in the Middle East, technology is transforming the way we live and work, and the United States has overhauled corporate taxation. Change brings opportunities, but it also presents risks.
5 key risks
So, what are the five key risks that should be at the forefront of risk managers’, CFOs’ and treasurers’ radars in 2018? And what are best practices for managing them?
1. Cybercrime
Cybercrime is an ever-growing and ever-present threat. It is a particular concern for corporate treasurers since the cash flows they’re responsible for are a key interest for most cybercriminals. In 2016, research by the Association for Financial Professionals found that almost three-quarters (74%) of the organizations that it had surveyed had been the target of attempted or actual payments fraud, including check fraud and unauthorized transfers of funds associated with business email compromise attacks. Almost a third (29%) of those that had been targeted by fraudsters had lost $250,000 or more.
Companies that don’t have the right systems in place to detect unusual or suspicious behavior may potentially end up exposing their organization to serious reputational damage and significant financial loss. Yet the Hiscox Cyber Readiness Report 2017 found that more than half (53%) of surveyed companies in the United States, U.K., and Germany were ill-prepared to deal with an attack.
Cybercrime cost the global economy over $450 billion in 2016. Risk managers, CFOs, and treasurers must talk to their technology vendors to make sure they are investing in the most effective security capabilities for their systems.
2. Rising interest rates and the end of cheap cash
For years, large companies have been able to borrow money at extremely low rates. In the seven years that followed the financial crisis, U.S. businesses were typically borrowing from banks at interest rates in the region of 3.25%, while the corporate borrowing rate in the U.K. dipped as low as 2.65% in 2009.
Even as recently as December 2017, the average interest rate in the Eurozone on a fixed bank loan of more than €1 million for a period of 10 years or more was 1.75%, according to the European Central Bank (ECB).
The clock is ticking on cheap money
In the bond markets, borrowing costs plunged even lower over the past decade. Some companies, including French pharmaceutical maker Sanofi and German consumer goods producer Henkel, even managed to issue negative-yielding debt.
However, the clock is now ticking on cheap money. The U.S. Federal Reserve has hiked interest rates five times since December 2015. Last November, the Bank of England announced its first hike in more than a decade.
The ECB is expected to follow suit, and the Bank of Japan is cutting back on its bond-buying program, suggesting that its rates, too, will rise in due course. Businesses should expect their funding costs to increase over the coming months and years. Highly leveraged companies can expect to feel the biggest squeeze.
To avoid unwanted questions from the board about the impact of the rising cost of cash, global risk managers, treasurers, and CFOs should look to refinance debt early and for an extended period in order to reduce their exposure to rising funding costs. They can also mitigate the risk of higher borrowing costs through effective cash management, by better utilizing global cash surplus balances to reduce short-term borrowing, and through due diligence on mergers and acquisitions (M&A) to make sure their company doesn’t overpay for a deal that it later regrets.
3. U.S. tax reform
As of the first of this year, U.S. corporate taxes were slashed from 35% to 21%. What’s more, the reform package includes a one-off repatriation tax on corporate earnings held overseas — 15.5% for liquid assets and 8 percent for illiquid assets — that is intended to encourage U.S. companies to bring home cash they previously stashed abroad.
On the face of it, the tax reform seems beneficial for foreign companies doing business in the United States, since their subsidiaries here will pay less tax. Yet some of the rules, including a base erosion and anti-abuse tax (BEAT) and a cap on the deductibility of interest, present challenges for some multinationals that move money back and forth across the U.S. border. CFOs and treasurers need visibility into their organization’s cash flows to and from the United States, and they should review its strategy for intercompany loans.
4. Brexit
Although the United Kingdom is set to leave the EU on March 29, 2019, there will almost certainly be a two-year transition period to smooth its departure. During this transition, the U.K. will have to abide by EU rules in the same way that it does today. The longer-term implications of the split are not yet clear, though, since a trade deal has yet to be thrashed out.
One area to keep an eye on In the past, U.K. regulators have had a great deal of influence over the EU’s financial services regulations. Going forward, there could be a divergence between U.K. and European banking rules — for example, in terms of how banks adopt the Basel III capital and liquidity standards.
According to PwC, the uncertainty associated with Brexit poses a number of specific challenges for treasurers, including foreign exchange volatility, possible funding shortages, and increased counterparty risk if companies have to suddenly develop relationships with unfamiliar financial institutions. The firm suggests that organizations put in place processes and systems which enable them to readily access their cash, monitor their treasury risks, adapt their financing strategies to changing markets, and manage their relationships with financial institutions.
5. Economic Shock
So far, the volatility that we’ve seen in the equity markets in 2018, can be better described as a correction than as a crash. Nevertheless, a catastrophe may lie around the next corner. It is no coincidence that the fall in equity prices coincides with the rise in bond yields that has come about as a result of governments buying fewer bonds. In early February, the benchmark U.S. 10-year Treasury bond hit 2.85%, its highest point in four years, as investors pulled out of equities.
The current market conditions have two significant implications for corporate risk managers and treasurers: First, as the yields on government bonds rise, it will become harder for companies to issue bonds with historically low coupons. And second, should a major stock market crash occur, it could dent consumer sentiment and cause both people and businesses to cut back on their spending, which would, in turn, squeeze companies’ cash flow.
Difficult market conditions may also prompt banks and bond investors to refuse to fund to companies that are seen as undesirable credits. Of course, it’s virtually impossible for a company to buffer itself from the full impact of a major economic shock, but sound working capital management can play a vital role in helping an organization to survive even the toughest of times.
A state of constant flux will continue to plague the global economy. In this environment, successful businesses will be those that are able to respond quickly.
Risk managers, CFOs, and treasurers who can’t capitalize on the opportunities presented by changes in the economy will put their organizations at risk of falling behind. Fortunately, effective cash management is a great foundation for long-term business agility, especially when combined with powerful technological tools such as in-house banking capabilities, notional cash pooling, and payment fraud detection systems.
Ultimately, change does not have to be a threat to organizations. By harnessing technology, smart companies turn it into a great opportunity to profit and grow.
Source: PropertyCasualty360
Author: Greg Person
Image: Shutterstock
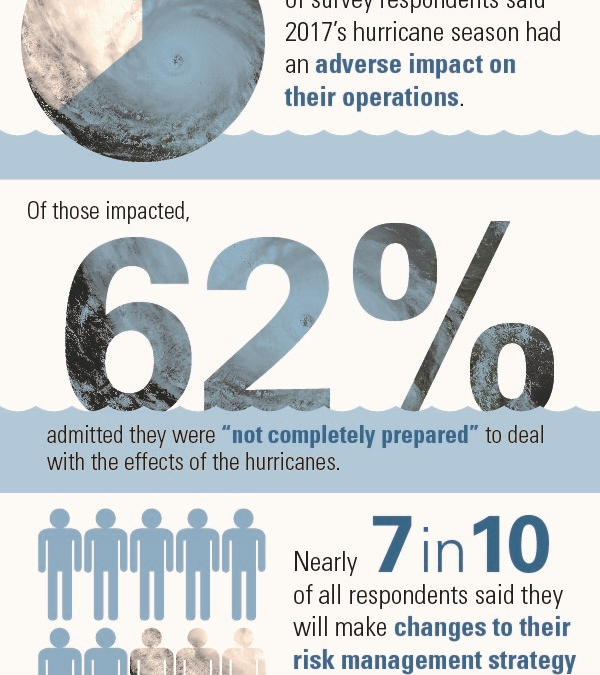
Feb 6, 2018 | Blog-All, RIsk Management News
A majority of senior executives of large U.S. companies with operations in Texas, Florida or Puerto Rico admit to being unprepared for last year’s hurricanes that devastated their communities, according to a survey by FM Global. While 64% of respondents said the hurricanes had an adverse impact on their operations, a full 62% said they were not fully prepared.
“These candid admissions drive home a fundamental truth about catastrophe,” Louis Gritzo, vice president and manager of research at FM Global said in a statement. “People routinely fail to understand or acknowledge the magnitude of risk until they’ve experienced a fateful event.”
One reason for a lack of natural-hazard preparation is imprecise terminology, he said. Being located in a “100-year flood” zone, for example, “does not mean you have 99 years to plan—but that there is a 1% chance of such a flood every year.” Another reason for insufficient preparation is over-reliance on insurance, which cannot restore the market share, brand equity and shareholder value lost to competitors.
The study found that as a result of hurricanes Harvey, Irma and Maria:
- 57% of all respondents said they will put in place or enhance their business continuity or disaster recovery plans.
- 40% plan to invest more in risk management, property loss prevention, and/or reassess their supply chain risk management strategy.
- 25% will reassess their insurance coverages or their insurers.
FM Global commissioned market research firm ORC International to survey 101 senior financial executives at Fortune 1000-size organizations by phone in October through November 2017.
Source: http://www.riskmanagementmonitor.com

Jan 30, 2018 | Blog-All, RIsk Management News
Businesses face many risks related to technology, including the risk of a cyber breach resulting in the loss of protected health information (PHI), personally identifiable information (PII) or payment card information. The threats are real, and the potential losses can be steep. The Ponemon Institute found in its 2017 Cost of a Data Breach report, that the average cost of a data breach in the United States in which customer privacy was compromised was about $7.35 million, or $225 per lost or stolen record.
Organizations may also incur losses through phishing (malicious email disguised as coming from a colleague, customer or financial institution to gain access to assets); ransomware (an attack that encrypts valuable information to extort funds from the victim in exchange for the data’s release); or a denial of service attack (an attack that cripples an organization’s online operations, preventing it from doing business). These scenarios were illustrated by the WannaCry and NotPetya global ransomware campaigns and the Mirai botnet DDoS attack that disrupted internet and e-commerce services in both the United States and Europe.
The WannaCry and NotPetya attacks were the broadest and most damaging cyberattacks in history. Like most ransomware, WannaCry encrypts a victim’s digital files until the victim pays for a key to unlock the files. Hackers often demand bitcoin payments of a few hundred dollars for personal files or thousands of dollars for business files. NotPetya was spread via the compromised software update service from a distributor of tax accounting software mandated by the Ukrainian government. Once NotPetya infects a system, it sets up encryption routines and attempts to spread over the network.
The Mirai attack was notable not only for its size and impact but also for the implications. Mirai hijacked the communications of hundreds of thousands of Internet-connected devices to carry out its attack. According to some estimates, there will be more than 20 billion such internets of things (IoT) devices in service by 2020. That is a significant increase in the number of connected devices currently in use, meaning there is a corresponding increase in the risk that security vulnerabilities will be exploited for similar attacks in the future.
Whether the result of a malicious attack, technical malfunction or human error, a data breach can trigger costs related to legal, technical response and forensics, crisis management, credit monitoring, and associated services. Financial losses can also be associated with a technical failure, or fines levied by regulators. In order to help mitigate the risk, cyber insurance can provide financial protection for out-of-pocket expenses arising from a data breach. A select group of carriers has also started to offer coverage for customer flight related to loss of brand trust.
Astute business leaders appreciate that cyber risk can be managed by coupling technology with risk transfer that protects the company and unlocks growth. A select few insurance carriers have also evolved their cyber insurance forms in order to provide coverage for losses that cause bodily injury and property damage that may have been caused by a breach of the network and/or system.
Cybersecurity should be managed as both a technical and economic challenge. It should also be viewed as an opportunity to improve performance and optimize capital efficiency—not just as a cost that needs to be managed. A quantitative analysis can enable companies to more efficiently allocate capital and other resources to reduce and manage cyber risks. In order to fill the gaps and provide financial relief from a data breach, companies are increasingly turning to insurance, especially as increasing competition among underwriters has driven prices surprisingly low, while the breadth of coverage being offered has expanded.
Cyber insurance premiums, which totaled an estimated $3 billion in 2016, are on pace to reach $20 billion by 2020, with more than 60 underwriters offering policies in a competitive marketplace with no standard forms, definitions, exclusions or conditions to follow when underwriting a cyber policy. These costs are in addition to the more than $80 billion a year that Gartner says businesses worldwide spend on technologies intended to protect both data and the systems where data are stored and managed.
The tumult of operating in a new market amid so many unknowns and variables means businesses should work with a cyber insurance expert who can accurately identify and inventory key assets, data, systems, and infrastructure essential to the business’s operations, quantify a business’ internal controls, and create a digital profile to identify internal vulnerabilities and external threats. Perhaps most critical is to work with a cyber insurance expert on quantifying a value of cyber assets at risk using modeling and technology tools.
Data protection is not easy and it is made even more difficult when investments in IT security are misallocated. Because technology and the threats posed by hackers evolve quickly, it is imperative organizations take the time to better understand their risk and to examine their networks for security vulnerabilities. Whatever an organization spends on technology, cyber risk management starts with a highly-trained and aware workforce. It is imperative to have a security-focused culture, reinforced through continuous training and positive reinforcement.
Itzik Kotler, co-founder, and CTO of SafeBreach said that there are a number of emerging trends that may introduce previously unknown risks and how keeping pace with these innovations is imperative to minimizing cyber risk. For example, Kotler recalled his own conversation with the chief information security officer (CISO) of a media entertainment company in the process of constructing a new office building that included features like smart lighting, smart blinds and other IoT-enabled devices connected to the corporate network.
Kotler said the CISO expressed concern about connected devices being compromised by a hacker. He was worried about the risks if the smart HVAC devices became an infection point, or worse, were used as a malicious cyberweapon. What if, for example, their data center servers were brought down because the air conditioning was no longer cooling the facilities?
According to the Ponemon study, 24% of breaches were due to human error. Despite the billions of dollars spent on technology, people make mistakes, cut corners, become reckless and are sometimes simply unaware that their behavior is outside the bounds of company policy.
In an age when doing business requires moving data from point-to-point, and every step of that process increases the level of risk for a data breach, there is little room for complacency. That is why it is imperative companies establish and enforce policies that teach their employees proper handling of data and for the introduction of new technologies—including hardware, applications, mobile devices and cloud-based services—into the enterprise.
From a technology standpoint, it is important to recognize that no business—big or small—is fully protected from a possible data breach. For organizations considering the addition of a cyber insurance policy to their risk management portfolio, the message is clear: Adding cyber coverage as a hedge against the financial costs associated with a data breach is an effective way of transferring that risk.
Source: http://www.rmmagazine.com

Dec 19, 2017 | Blog-All, RIsk Management News
When it comes to record management and customer notifications, the legal requirements for businesses are vastly different from state-to-state. Take for example California, where businesses are required by law to immediately notify a state resident if his or her personal information has been acquired by an unauthorized user. Most states have similar laws. In Alabama, however, there is no state law requiring a business to notify customers of a data breach.
But only doing the bare minimum of what is legally required can still leave your business vulnerable to reputational harm, loss of customers and disruption of business processes that may prove catastrophic in the long run. Ask yourself this: If it were your data stolen, would you want or even expect to be notified?
What Constitutes a Customer or Employee Record?
In 2016, more than 4,000 data breaches exposed over four billion records. But what exactly are we talking about when we are referring to “records” that have been exposed?
In general, data collected on customers and employees falls into three basic categories:
- Health Information such as records from a doctor’s office or human resources department
- Banking Information such as credit card, debit card or bank account numbers
- Personally identifiable information (PII) or data that can identify the person, the person’s location or other private information
It is often this last category, PII, that causes the most confusion. The federal government and many states have taken a stab at clarifying what constitutes PII and these definitions vary wildly.
Take a moment and think about the information you require from your customers or employees, or even think about the type of information you provide as a customer yourself. Everything from your password, answers to your security questions, your shipping address or even your driver’s license number is an identifying piece of information.
With just an email address and answers to common security questions, a cybercriminal can reset a password to a customer’s email account and gain access to their inbox, which can lead them to social media profiles or Netflix or iTunes accounts that house credit card or bank account information. But that’s not all. Just because your business was not directly impacted by the breach itself, your business may still be held liable for those stolen records, even if the records were stolen from a vendor.
While each state might have differences of opinion regarding which specific pieces of data you collect are legally protected, will your customers feel the same?
What Are the Risks Associated with Your Business Records?
There are two major risks when a business gathers and stores customer and employee information.
The first is to your customers and employees. Not only can there be a risk of financial harm if the right information gets into the wrong hands but an individual’s privacy and security can also be exposed. As a business, it is your responsibility to know what information you have and to notify your customers and employees—whether or not you are legally required to so by your state—if you have been breached. This is expensive and has to be done immediately and done right.
The second risk is to the reputation of your company after a breach. How you handle the moments after a breach can impact how your customers or employees react once they find out their personal and sensitive information may have been exposed. Having the right type of support after a breach can make or break a business.
What Actions Should Companies Take?
Having a clear understanding of what type of personal and sensitive information you have stored on your business’ computer system and other electronic devices is a must. The same is true for vendors that may house customer or employee data on your behalf. Maintaining an inventory of the information you have on-hand is important, especially if your business has been a victim of a breach so that you can accurately notify your customers or employees of the information that has been exposed.
To properly protect a business today you need a robust cyber insurance policy, not just any cyber policy. Any cyber policy might have customer notification costs included in your policy but a good cyber insurance policy will:
- Provide notifications for all your customers even if you are not legally required to do so as well
- Pay to maintain your great reputation in the marketplace should a breach occur
- Include forensics to determine how this happened in the first place and fix it
Another important part of coverage when choosing a cyber policy is business disruption coverage. Many businesses never fully recover from the lost business following a breach. Be sure this coverage is included in your policy. According to a 2016 study conducted by Keeper Security and Ponemon, businesses that have been victim of a breach have lost an average of $955,429 due to the disruption of normal business operations, in addition to the average cost of $879,582 companies have spent due to damages (i.e., impact of business reputation or loss of trust from stakeholders) or theft of IT assets after a breach. Can your business sustain that loss without the insurance to cover it?
By having a clear understanding of what type of records you are collecting and storing from your employees and customers, along with a good cyber policy, every business owner can rest assured that if they are a victim of a cyber attack, they have the know-how and support of their insurance provider to keep their business running smoothly with the least amount of damage to business processes and reputation.
Source: http://www.rmmagazine.com

Nov 8, 2017 | Blog-All, RIsk Management News
Newer developments like a 3-D laser and sensor technologies are enabling contractors to build in a smarter and safer way. Insurers should understand where the construction industry is headed in terms of technology use and how emerging devices can help improve both physical construction sites and worker safety.
Imagine being in the middle of a large-scale office tower build, with the framing, exterior walls and roof all finished when you notice the structure’s support beam measurements appear to be wrong. Instead of going back to the architect and engineers involved in the project to confirm measurements by hand, and potentially stalling the build of the project, you use a 3-D laser scanner that in a matter of moments confirms the design measurements are on point and you won’t have to delay the build.
This is just one scenario that captures the challenges contractors face today and how the construction site of the future, which will focus on harnessing data and technology together, can ultimately help contractors build in a smarter and safer way.
Building smarter
For construction companies working off an architect and engineering professional’s plans, measurements could be incorrect. When transforming a warehouse into a restaurant, for example, accuracy is highly important. Moving gas and water lines and electrical, and designing a kitchen out of an open space by hand leave potential opportunity for error, which could also cost the contractor time and money. If a measurement is off by even 10 inches, this apparently small mistake could potentially lead to great costs in rebuilding. In fact, according to the American Society of Civil Engineers (ASCE), the direct costs from rework can often account for 5% of the total construction costs, which is not always insurable.
3-D laser technology captures a construction site’s lines by creating an accurate, to-scale model of the different points of the scale, including space, air, and objects. This technology measures the site down to the millimeter.
Laser technology not only provides fast, accurate measurements but also can confirm whether the measurements are in fact correct. The technology matches the architect’s design against the physical building, providing an overlay of the measurements and highlighting areas where they do not align.
Contractors seeking to build with speed and accuracy use this technology to help identify problems in real time, revolutionizing how construction companies are approaching a build. According to a report from MarketsandMarketsTM, the 3-D scanning technology market is forecasted to grow at a significant rate for the architecture and construction industry industries between now and 2023.
Future applications of 3-D technology largely fall into two categories:
Using a 3-D laser scanner on a drone: Imagine being able to have a drone scale an 80-story building in minutes while confirming measurements and accuracy from the sky. A daunting and high-risk scenario becomes a relatively easy and much safer task.
Virtual reality and augmented reality: Contractors can scan the physical building against the design, creating either a virtual reality hollow so that workers can see where pipes will go or augmented reality visuals where architects, engineers, inspectors and even homeowners can see progress on a building in real-time. 3-D scans can be overlaid against the Building Information Modeling design to provide a real-time comparison of the current build against the original design
Protecting the physical site
Among the new technologies that are currently available, mobile sensors – the size of a paperback book – can be deployed on construction sites to help detect the building’s temperature, humidity, dust particles, noise, vibrations, among other things. By monitoring the building’s environment, contractors can receive real-time alerts when the building reaches certain thresholds.
By way of example, let’s say the temperature drops in an office tower construction site. With mobile sensors, the contractor can immediately receive an alert giving them an opportunity to check on the tower. Something as simple as a pipe bursting in the middle of winter because a door was left open can lead to significant losses.
As sensor technology advances and the market becomes more competitive, we will likely see more robust sensors on the market that are able to monitor the building’s holistic environment.
Workplace safety
Wearable sensors are another example of emerging technology – similar to the popular bracelets that track one’s physical activity or a pedometer that measures the steps someone has taken in a day – sensors are now being tailored for construction site workers to provide real-time data with the goal of increasing workplace safety.
Construction sites are a high-risk work environment. In fact, some of the most common injuries experienced on construction sites include strains and sprains, falls from elevation, and those related to heat stress. Repetitive motion injuries such as bending or lifting are also common.
Most insurance carriers today offer risk management consultants who can go onsite and provide construction clients with a snapshot of potential risks, observations, and insights into indicators that can potentially lead to workplace injuries. Wearable devices are essentially a safety professional standing behind each worker all day, every day, monitoring whether workers are bending correctly or if the site’s temperature is placing them in a heat stress environment. The technology could also connect to claims data so insurers can provide insureds with proactive proposals and solutions to help change workers’ behavior to reduce the potential for injuries.
In the future, wearable technologies will be able to harness forensic data and other information from the physical construction site as well as historical claims, while also receiving real-time data that can provide predictive analytics.
Smart sites of tomorrow
Construction sites and the construction industry as a whole represent a prime case for technology disruption. In the next 5-10 years, it is probable that all of these technologies will be capable of connecting and talking to each other while outputting data into a single monitoring system that can be used by construction companies, insurers as well as architects and engineers to help take proactive actions.
A 2016 report from McKinsey & Company found that large construction projects typically take 20% longer to finish than scheduled and are up to 80% over budget. But thanks to the construction site of the future, using 3-D lasers, mobile sensors, and wearable technology could ultimately help provide a safer, more efficient workplace and, in turn, reduce costs.
If the industry develops a solution for construction sites, it can be applied to other industries such as manufacturing, logistics, warehousing or healthcare. As economies of scale also take hold, we could see the cost of these technologies decrease and the barriers to embracing these technologies start to dissipate.
Source: PropertyCasualty360
Photo: Shutterstock






