
Feb 23, 2017 | Blog-All, Informative
Claims digitization will be the over-riding theme for 2017 as these capabilities touch every aspect of the claim landscape. A review of some of the more costly events in 2016 highlights the role of technology and its impact on all areas of claims going forward.
Natural catastrophe events in 2016 dwarfed those from 2015. Per Swiss Re, the first six months of 2015 resulted in a total loss of $46 billion (US) in natural catastrophe events. For the same period in 2016, $68 billion (US) in natural CAT losses were realized — an increase of almost 50 percent. Earthquakes in Ecuador and Japan, wildfires in Canada, and flooding in Europe, all contributed to what will amount to a very large CAT loss year.
From a consumer point of view, overall loss costs from 2010 to 2015 declined by 30 percent for US-based homeowners across a broad number of areas, including wind events (down 50 percent); hail by more than 20 percent; fire (steady decline, no figure available); and theft loss costs, which decreased by 50 percent.
Several factors will impact claims in 2017, ranging from new technology such as autonomous cars and drones to applying analytics to the claims process itself. Among those that will have the greatest influence are:
1. Market trends: autonomous cars
The emergence of self-driving cars will continue unabated into 2017. It raises questions of liability regarding the self-driven car ecosystem — with computers, sensors, software and intelligent infrastructure taking more responsibility for the operation of the vehicle, how will culpability for accidents be determined?
In our current reality, liability accrues to the driver of the vehicle that caused the loss event, however that is determined. With a physical driver relegated to being a monitor of an automated process, this does not seem to be the best way to determine fault going forward.
2. Big data
Our ability to collect and disseminate data has never been more prolific, and that will escalate into 2017 and beyond. Sensors now exist, and the communication infrastructure has evolved to the point where data can be gathered, communicated and analyzed very quickly to arrive at informed decisions/recommendations around potential loss events. This capability can help drive down the severity of the loss event and increase the probabilities of stopping the loss before it occurs.
3. Cyber liability
Cyber liability continues to be an area of increased focus for insurers, and most offer cyber liability products to policyholders that are primarily aimed at the loss of data due to an intrusion. However, there were developments during 2016 that suggest loss of data and the costs to recover it may be far from sufficient.
For example, recent losses in the Iranian oil fields due to orchestrated cyber attacks need to be examined closely. These cyber attacks resulted not only in data loss, but also in physical buildings and contents lost through fires and explosions proximately caused by the intrusion.
This is a whole new realm in the cyber liability arena, and one that most insurers are not including in their products for this space. This claim and loss issue will command significant attention going forward.
4. Claims core systems: Ready for a comeback?
Pivoting to the technology front, although claims enterprise system replacement or augmentation dominated in 2005–2012, the focus by insurers more recently has been on policy and billing administration systems. However, claims-driven technology capabilities are again receiving attention, primarily in the areas of digital capabilities. While the prior activity resulted in a significant increase in claim process automation, there remain significant gaps in analytics, augmentation of internal insurer data with third-party data, and collaboration amongst the eco-system players in claims.
First Notice of Loss (FNOL) processes and the collection of information by the claims adjuster still involves significant time and entry of data. One clear trend addressing this is the increasing use of robotic process automation (RPA) to automate data entry activities. If done correctly, RPA replicates the activity of a human in standard data entry by gathering data from multiple sources, standardizing and formatting the data for ingestion, and applying it to the appropriate aspect of the workflow.
5. Applying predictive analytics and AI to claims
There are also many opportunities in the claims process for the use of predictive analytics, although adoption has been slow. There are clear use cases for specific areas — including claim fraud and loss and reserve forecasting — and clear areas of opportunity such as loss forecasting. The benefits of quickly assessing a claim’s severity, forwarding it to the proper claim expert, involving all applicable claim services, and coming to a fair and expeditious settlement to avoid litigation are clearly understood. One key area enabling accurate loss forecasting analytics is the incorporation of sensor-driven data — such as from boilers or related energy-producing vessels where heat, pressure, load and other key data elements can be monitored.
Predictive analytics can also help to prevent fraud. These predictive tools are used to identify data elements likely to or potentially leading to fraud, e.g., auto collision claim coming in from New York City from areas with high congestion; late model sports cars; accident types that suggest fraud (such as rear-end accidents with neck injuries). All these factors tell a story, and predictive tools can help analyze that information.
6. Artificial intelligence
Another technology enabler in claims that will receive increased focus in 2017 is artificial intelligence (AI). Coupled with image and video analytic tools, AI can “learn” how to provide increasingly accurate loss estimates based on a picture or video. Of course, AI has other areas of application in the claims value chain. Subrogation and salvage are two technical areas within claims that will benefit from having AI applied to the existing analytical models; subrogation, specifically, is an area that many insurers feel is under-utilized and sub-optimized.
7. Prioritizing process optimization and customer engagement
Optimizing the overall claims process for policyholders will be another key focus for 2017. Automation efforts in the past decade focused on automating and consolidating internal claims activities. Now, providing smart, easy-to-use and intuitive capabilities for external audiences, like policyholders and claimants is being addressed.
One of the key touch points with customers is in paying their claims, an area critical to customer satisfaction and policy renewals. Start-ups in the insurance space are using automation to address the claim payment process (as well as the quote and purchase process).
Lemonade and Trov are both making the claims process as painless as possible for their insureds. Trov is using text messages to provide a basic “First Notice of Loss” channel. Lemonade accepts a picture or video of the damage, and attempts to adjudicate the claim based on that information and a series of algorithms, as well as information from the policyholder.
8. Drones
Drone use is another utility that is going to make a significant difference in commercial claim processing for instruments that are difficult, expensive or even dangerous to perform damage assessment upon. This includes: bridges, oil well derricks, cell towers, tall smokestacks, and radio and TV towers, which are difficult to access for direct observation and measurement of damage due to hail, wind, precipitation and the like.
Drones provide highly detailed images that can be used for image analytics to assess damage. Having both pre- and post-loss imagery will provide for better damage estimates. The images also can be used to estimate other parameters such as height, distance from other physical objects like bodies of water adjacent to properties. With FAA regulatory clarification, the use of drones in commercial insurance will increase significantly and use cases for personal lines will emerge as well once FAA regulations are fully implemented and understood.
9. Blockchain
Finally, the reverberations from the blockchain technology wave will be felt in the claims process. At a minimum, the potential for reducing fraud in fine arts, classic cars, and related high-value insured objects sector will be significant. If blockchain can be leveraged to create public ledgers where high-value objects are identified and tracked, the occurrence of forged items should diminish over time. There are also potential benefits in areas such as title insurance, where title information can be shared in a public ledger available to multiple parties of the insurance and real estate transaction.
Adopt a test-and-learn approach
There were many opportunities in 2016 to apply digital capabilities to the claim process, and that will only increase in 2017. As with any investment, keeping the business case in mind is always important; however, insurers should take a “test and learn” approach and not expect immediate returns on their investment. The learning aspect will be valuable, and should be recognized as a “benefit” too.
Sources:
PropertyCasualty360
iStock
Article: by Tom Rubenacker

Feb 15, 2017 | Blog-All, RIsk Management News
In order to be effective, an organization’s risk management plan requires the development and maintenance of an ongoing process that enables the identification, analysis, evaluation and treatment of relevant risks. This knowledge better enables risk professionals to prioritize actions to reduce these risks to an acceptable level. What results from this risk assessment process, however, is a substantial amount of risk information that needs to be managed in such a way that it can be found and applied quickly and efficiently. This has led to the creation of risk registers.
A risk register is a document that records identified risks, their severity and the mitigating steps to be taken in response. It serves as a central repository for the organization’s risk information and allows for the information that results from the risk management process to be suitably sorted, standardized and merged. A risk register’s key function is to provide management, the board and key stakeholders with information about the main risks faced by the organization. The register also gives the organization’s risk management stakeholders a clear view of the status of each risk at any point in time.
Once a risk register is created, however, a question that can arise is whether or not it is discoverable in litigation and whether the information contained within these internal documents is protected by the attorney-client privilege and work product doctrine. As a result, in-house and/or outside counsel must be cognizant of how a risk register is prepared and maintained in order to solidify a company’s claim to privilege.
When a written risk register has been prepared by a non-lawyer, the potential protections from discovery are limited as organizations will not be able to rely on traditional discovery protections such as trade secret or work product for these documents. One potentially applicable protection is the “self-critical analysis” privilege, which protects analyses of a company’s own safety procedures.
In New Jersey, for example, in order to raise the self-critical analysis privilege, a company must show that: 1) the information that is the subject of a production request is the criticisms or evaluations or the product of a critique or evaluation conducted by the party opposing the production request; 2) the “public need for confidentiality” of this analysis is such that the unfettered internal availability of the information should be encouraged as a matter of public policy; and 3) the analysis or evaluation is of the character that would result in the termination of such self-evaluative inquiries or critical input in future situations if this information is subject to disclosure.
Alternatively, an organization can attempt to protect an internal risk register from disclosure by employing outside counsel to manage and create it. Under this circumstance, outside counsel is retained by the organization to provide legal advice regarding vulnerabilities, and to develop a strategy for risk minimization. As part of this process, outside counsel, rather than the organization, can retain an independent consultant to assist in the due diligence analysis and in the preparation of the risk register. The consultant’s report would be prepared at the request of counsel, which would then be incorporated into a more comprehensive report for the organization by the attorney. Accordingly, a company would be in a position to assert that the risk register, including the results of the outside consultant, are protected by the attorney-client privilege.
In the context of cyberrisk, an internal risk register requires companies to: 1) conduct network vulnerability assessments; 2) provide recommendations to remediate potential vulnerabilities; 3) review cybersecurity policies and procedures; and 4) review its internal network. Whether companies that suffer data security breaches may claim attorney-client privilege and/or work product protection in connection with these documents and communications is often disputed. For example, if a company prepares an internal risk register that identifies areas of vulnerability and concern but fails to remedy the problem, this would clearly provide sufficient evidence of notice to establish a claim for negligence against the company. Conversely, if an internal risk register supports the conclusion that a company’s internal network is safe and secure, yet it is subsequently breached by a hacker, this assessment could also be used against the company in litigation.
In In re Zappos.com, Inc., Customer Data Security Breach Litigation, for example, the Zappos website declared that “shopping on Zappos.com is safe and secure—guaranteed.” Following a data breach, plaintiff consumers used this statement as a basis to overcome a motion to dismiss based upon a theory of negligent representation. They argued any statement made within an internal risk register regarding areas of concern or the safety and secureness of a company’s internal network could be used against the enterprise making such representations.
Similarly, the plaintiffs in a class-action lawsuit filed after a massive data breach at insurer Anthem served the federal government with a subpoena requesting that they share documents from a security audit proving Anthem was aware that its information technology security was lacking before the breach occurred, and did not act on the risk. The U.S. Office of Personnel Management, which performed the audit, refused to release the results, claiming the information contained in its report is privileged and immune from disclosure.
A recent decision in litigation over the data security breach suffered by Target Corp. sheds important light on the scope of such protections. In In re Target Corp. Customer Data Security Breach Litigation, the court found that Target submitted several declarations and exhibits to substantiate Target’s privilege and work-product claims as to its response program. Following the large-scale cyberattack on Target, a two-track response program was created, one involving a team of forensic experts who were engaged on behalf of several credit card companies, and the second to assist counsel in conducting an investigation of the data breach in order to provide legal advice to Target.
During discovery, Target produced all communications with forensic experts from the first track, but withheld communications and work product prepared by the data breach task force and experts engaged by counsel as part of the second track. In denying the plaintiffs’ motion to compel the discovery from Target, the court held that the work of the second track was focused not on remediation of the breach, as plaintiffs contended, but on informing Target’s in-house and outside counsel about the breach so that Target’s attorneys could provide the company with legal advice and prepare to defend the company in litigation. Moreover, plaintiffs could not overcome Target’s work-product protection because Target had already produced documents and forensic images from which plaintiffs could learn how the data breach occurred and about Target’s response to the breach.
Although this opinion relates to internal investigations following a data breach, the same principles can be applied to the preparation of risk registers. Namely, these reports should be prepared at the request of the counsel to provide legal advice to a company, and to help defend against the threat of litigation should an incident occur.
While risk registers can provide an organization with valuable information about identifying and remedying potential areas of exposure, they can also be a distraction. Importantly, the risk registers may contain highly sensitive information that, if left unattended, may be used against the company in subsequent litigation. As a result, an enterprise should work through internal and/or outside counsel when preparing risk registers so that the sensitive risk information obtained may be protected by the attorney-client privilege and work product doctrine if litigation later ensues involving one of the identified risks.
Source: RMMAGAZINE.COM

Feb 1, 2017 | Blog-All, Informative
It’s tax time, and that means fraudsters are once again using phishing and deception to trick those who have access to staff member’s W-2 tax forms into turning them over.
The tax forms are a treasure trove of information, including employees’ names, addresses, Social Security numbers and wages, that can be used to commit fraud, such as filing fake tax returns to obtain a refund.
Among the organizations that have recently fallen victim to phishing scams involving the inappropriate release of W-2 data are Campbell County Health of Gillette, Wy., and eHealth Inc., an online health insurance exchange based in Mountain View, Calif.
These type of scams, which pop up at the start of every year, point to the need to enforce corporate policies against sharing W-2s and other sensitive personal information via unencrypted email under any circumstances and to educate all employees to be on the lookout for fraudulent requests for information.
Campbell County Health Targeted
In a Jan. 25 statement, Campbell County Health, which operates a 90-bed acute care community hospital and other facilities, acknowledges that it was the victim of a “security incident” that may affect some of their employees’ personal information.
“Currently, it appears that an unauthorized individual, impersonating a CCH executive, contacted an employee requesting W-2 information for all of our employees who had taxable earnings in calendar year 2016,” says Andy Fitzgerald, CCH CEO. “Unfortunately, before it was determined that the request was fraudulent, the employee provided these files.”
“CCH has contacted local law enforcement and a cybersecurity response team, both of which are actively working to identify the fraudulent party and help the organization take all necessary actions to protect their employees,” Fitzgerald says.
The county healthcare provider says it has informed its employees of the steps that they can take to guard against fraud or identity theft, such as monitoring their bank accounts, credit cards, tax returns and other personal or financial information, as well as contacting major credit bureaus. CCH also says it will offer its employees free identity protection services.
“We take this matter and the security of personal information very seriously at CCH, and we will continue to review and enhance our security practices to further secure our systems,” Fitzgerald says in the statement.
CCH did not immediately respond to an Information Security Media Group request for comment on the incident. But a local news outlet, the Gillette News Record, reports the breach affected about 1,400 CCH employees.
eHealth Inc. Incident
Meanwhile, a sample data breach notification from eHealth posted by the California attorney general’s office indicates one of its employees also fell for a similar trick on Jan. 20.
The notice says an eHealth employee received a phishing email that the individual thought was “a legitimate email” from a company executive. Before the company discovered that the request was made from a fraudulent email account, the employee had already sent copies of eHealth employees’ W-2 tax forms.
The notice does not indicate how many eHealth employees were impacted, and eHealth did not immediately respond to an ISMG request for information. The company is offering affected employees free credit and identity monitoring services for 24 months.
Tax-Related Scams
Mac McMillan, CEO of the security consulting firm CynergisTek, says phishing schemes involving W-2s are just the tip of the iceberg when it comes to tax season scams.
“These are not new attacks. They unfortunately happen every year prior to tax time,” McMillan says. “Worse yet – tax fraud from fraudulently filed returns accounts of several billion dollars in losses every year, and a considerable amount of inconvenience and in some cases financial stress for victims.”
To help combat these kinds of phishing scams, “one simple thing they can do is remind their financial staffs and their employees that these types of events occur every year and not to fall prey to them,” McMillan says. “Remind them that the CEO will never request this type of information from them in an email, and they should not respond to such a request without first verifying its authenticity. Awareness is key.”
Privacy and security expert Kate Borten, president and founder of the consultancy The Marblehead Group, says organizations need to adopt clear-cut policies on what types of information cannot be transmitted, under any circumstances, via unencrypted email.
“There should be limitations on transmitting such data via email [that’s] unencrypted,” she says. “You can’t blame it all on training if the underlying policies are inadequate.”
McMillan says phishing email scams can be difficult to battle. “But with the right technology in place, the right filters enabled, they can be easier to spot,” he notes.
“The user still needs to be alert to requests of this nature, though, and not just click on or answer requests, regardless of who they come from, to provide personal information. This particular scenario can be managed by having an iron clad rule in finance that says no matter who sends such a request, the information is not to be provided until specifically approved by a manager or the CFO, and the request is verified with the sender. That ensures that more than one person reviews the request and there is a higher likelihood it will be discovered as a fraud.”
But when an employee does fall for these kinds of tax-related scams, it’s important to take action as soon as the mistake is detected to help avoid further fraud, McMillan notes.
“The first step is to report it to law enforcement, the IRS and their finance office,” he says. “Once alerted, steps can be taken to flag the persons’ returns if not filed yet. If the scammer has already filed the return, steps can be taken to stop its processing.
“If, worst case, [the tax return] has already been filed and processed, they will still need to report it to begin the process of recovery. They will want to do this as soon as possible as it typically takes a while for these matters to be resolved.”
Source: InfoRiskToday

Jan 25, 2017 | Blog-All, Informative
Hurricane Matthew — which wreaked havoc in Florida, Georgia and South Carolina and flooded large portions of North Carolina in 2016 — is a grim lesson on why companies need business interruption insurance.
The hurricane damaged or destroyed more than one million structures and cost $10 billion in damage.
Although the theme parks in Central Florida shut down for only a few days, businesses in flood-ravaged North Carolina were much slower to reopen.
By the time meteorologists identify a hurricane nearing the country and give it a name, it’s too late. Insurance coverages are already set, and businesses are forced to wait out the storm to see what damage it does.
Recent hurricanes, floods and earthquakes are a good reminder for businesses to review insurance policies to make sure they’re covered in the event of a natural disaster. Here are a few things to consider.
Don’t underestimate how long business will be interrupted.
When reviewing business interruption insurance options, it can be tempting to save some money and choose less coverage, especially if a business hasn’t lived through a hurricane, earthquake or flood. It’s easy to underestimate how much damage can be caused and how long a business will actually be interrupted.
Almost 40 percent of small businesses don’t reopen after a disaster because they’re not properly covered. In some cases, a business may reopen just a few days later, but it could feel the effects of the event long after it’s back up and running. Business owners, review your policy limits now to make sure they’re adequate. Make sure your coverage includes extra expense as well. It’s best to be as prepared as possible.
Make sure suppliers are covered.
A business might not be directly affected by a hurricane or earthquake, but its suppliers might be. Business owners, if you can’t get raw materials to make your products, or if you can’t deliver them, you might need contingent business interruption (CBI) to cover your suppliers. Contingent business interruption will reimburse lost profits as a result of a disruption in your supply chain. Review your policy now to assess what weather events trigger all of your business interruption coverages and the limits provided.
Review payroll coverage.
If a business has been impacted by a storm, operations might be stalled for several weeks or months. If a business employs skilled professionals, it likely wants to ensure that they can continue working when the business is back up and running. If a business requires people to work in a specific location or with specific tools, business owners want to ensure talent is paid while the business is being rebuilt.
It’s important for a business to determine which classes of employees should be covered during a period of restoration and any exceptions to employees are addressed and defined appropriately covered as “ordinary payroll” under business interruption coverage as well.
Create a disaster recovery and communications plan.
In addition to making sure that a business has adequate insurance to cover necessary repairs and rebuilding following a weather event, it’s vital to have a disaster plan that covers technical aspects of what’s needed to get the business up and running again. Similarly, owners need a communication plan that outlines how to alert employees about the status of the business.
Often, businesses’ insurance policies are not top of mind until an actual loss occurs. However, it’s important to review policies and plans regularly to make sure they align with current business. For example, if a business is going through major growth, you may want to ensure its business interruption policy adequately covers the loss of expected revenue.
If a business makes organizational changes, they may want to revisit who is and is not covered under payroll insurance. Putting these policies into place now, and learning from the mistakes of others, can help you deal with a disaster if — and when — it strikes.
Source : PropertyCasualty360

Jan 17, 2017 | Blog-All, RIsk Management News
A survey of more than 1,200 risk managers and corporate insurance experts in over 50 countries identified business interruption as the top concern for 2017. According to the sixth annual Allianz Risk Barometer of top business risks, this is the fifth successive year that business interruption has been seen as the biggest risk.
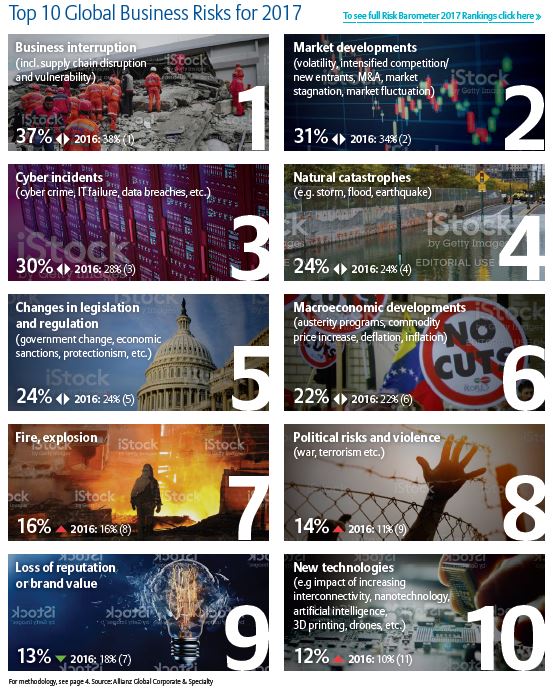
“Companies worldwide are bracing for a year of uncertainty,” Chris Fischer Hirs, CEO of AGCS said in a statement. “They are concerned about rather unpredictable changes in the legal, geopolitical and market environment around the world. A range of new risks are emerging beyond the perennial perils of fire and natural catastrophes and require re-thinking of current monitoring and risk management tools.”
While natural disasters and fires are what businesses fear most, non-damage events such as a cyber incident, terrorism or political violence resulting in denial of access are moving higher up on the scale, according to the report. These types of incidents can cause large loss of income to companies, without actual physical loss.
The second concern, market developments, could result from stagnant markets or M&As, or from digitalization and use of new technologies.
CyberRisk, third on the list of perils, has jumped up from 15th place in just four years. Cyber was identified as the second concern in the United States and Europe.
Source: RiskManagementMonitor

Dec 28, 2016 | Blog-All, RIsk Management News
Technology is changing the way we interact with the world, whether it is newer and smarter vehicles, a greater ease of communication, or an increase in the data available to help companies better target their marketing towards consumers. The rewards of these technological leaps, however, also come with some rather large risks, or at the very least create issues that have yet to be addressed.
The auto insurance industry is as vulnerable to these risks as any other industry. However, here are three major trends in the auto insurance industry likely to be of concern in the coming months. Technology has the potential to disrupt the insurance industry in a short period of time and companies must determine how best to adapt to the ever-changing technological landscape and use it to their advantage.
Automated vehicle technology
Automated driving is a broad concept, encompassing a myriad of technologies, some currently in production and others still in the imaginations of the world’s top creative engineers. The concept of autonomous cars is constantly evolving and has not reached full automation. However, further development of automated functionalities is inevitable.
While there are many benefits to automation, the technology is advancing faster than the legal and regulatory environments that govern it. Are insurers prepared for the impact of automated driving technology on the auto insurance industry?
One of the major benefits of automated vehicle technology is its ability to reduce the frequency and severity of auto accidents. This benefit will impact both the need for liability insurance and the number of claims submitted under insurance policies. As these technologies become mainstream, the personal lines auto insurance industry is projected to shrink by as much as 60 percent. A wholesale reevaluation of what is covered under auto insurance policies will be needed long-term. More immediately, insurers will be forced to address how automated technologies impact discounts, underwriting, apportionment of liability and claims handling procedures.
Another concern involves its propensity to be hacked. New technology creates unique cyber vulnerabilities that are unprecedented in the auto industry. The data connections and sensors critical to automated driving technology open the door for hackers to conduct cyberattacks that can compromise the security of the data collected, as well as the safety and operation of the vehicle itself.
Attacks that threaten the integrity of a vehicle’s safety operations pose a significant risk to personal safety, but interception of the data collected by the vehicles presents an equally significant economic risk. Who is responsible for accidents that are caused when a vehicle is hacked? Is it the driver, the manufacturer of the vehicle, or just the hacker? Will insurance coverage be modified to cover cyberattacks? If so, under what circumstances? These hypothetical questions are largely unanswered at the moment, but as the technology emerges, insurance companies will be forced to address them.
Distracted driving
Technology is not just affecting the automotive industry, but virtually every facet of our modern economy, and no consumer technology is more ubiquitous in American culture than the smartphone. At any given moment, approximately 660,000 drivers are using cell phones or electronic devices while driving, drawing greater attention to distracted driving.
Plaintiffs in personal injury claims arising from auto accidents have sought to place blame for distracted driving on the deeper-pocket cell phone manufacturers and app developers. Although many of these cases have had little success, some are gaining traction. For example, a car accident victim sued Snapchat, alleging it was liable for an accident caused by a driver who was using the app’s “speed filter,” which allows a driver to include a speed along with the driver’s picture. The plaintiff alleged that the “speed filter” not only distracted the driver, but also encouraged her to speed. The outcome of the case remains unclear, but if the plaintiff is successful, the decision could harken a wave of lawsuits against cell phone manufacturers and mobile app developers for damage caused by distracted drivers.
Insurance companies should pay attention to how the law develops on this topic since it could provide insurers with a mechanism for seeking contribution or indemnification from larger entities like cell phone manufacturers or mobile app developers.
Insurers’ reliance on big data
Although not a new trend, 2016 showed a continuing reliance on “big data,” or large amounts of consumer information culled from various locations and compiled into a neat package. Insurance companies use big data to engage in predictive modeling, particularly in underwriting, pricing and claims handling.
Big data can help with price optimization by being able to drill down into more specific segments of the population, or even marketing to particular individuals based on their consumer activity.
However, the downside for insurance companies is the potential for discrimination claims as demographics are used to drive pricing of certain insurance products and the claims arising under those policies. In particular, regulators are concerned that certain big data modeling factors may be correlated with prohibited rating factors. Insurance regulators will continue to focus on regulating the use of big data and price optimization going forward.
Each of these risks will affect how insurers write auto coverage going forward. Considering their impacts today though, will allow them to develop products that continue to protect policyholders well into the future.
Source: PropertyCasualty360
Pictures: ShutterStock







